- Navixy introduces two-factor authentication (2FA) for end users to enhance security for web and mobile applications.
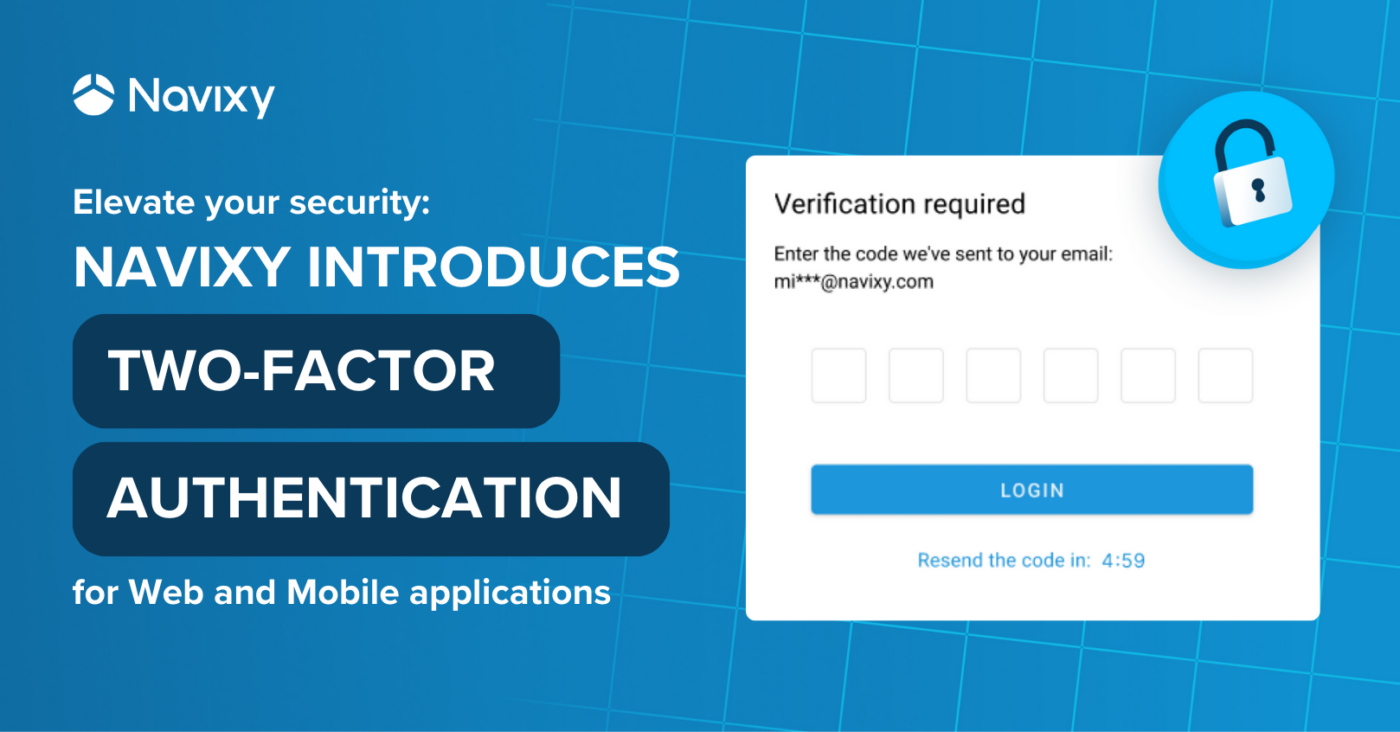
- Users will be able to verify their identity with a one-time passcode sent via email, adding an extra layer of protection.
- Administrators can secure user accounts with 2FA in bulk or enable it for specific accounts, depending on their client's security requirements.
Traditional login methods, relying solely on a username and password, are vulnerable to various attacks, such as password guessing and phishing attempts. As more IoT data is collected and stored on the platform, additional protection from unauthorized access is required. Recognizing the growing need for data security, we are introducing two-factor authentication for our web and mobile applications. All Navixy partners now can provide two-factor authentication for their clients, depending on their needs and security requirements.
According to Denis Demianikov, VP of Product Management at Navixy, this security measure has been highly anticipated, and adding it was a matter of time.
Introducing two-factor authentication (2FA) was a natural step for Navixy to meet the growing demand for safeguarding sensitive telematics data. By requiring a one-time passcode sent via email, 2FA provides significant account protection with minimal user input. This security level-up provides more confidence for our users that their data is better protected from unauthorized access.
– Denis Demianikov, VP of Product Management at Navixy
Why has two-factor authentication become a must have?
The two-factor authentication (2FA) solutions market is growing due to higher demand for secure products, technological advances, and expanded distribution channels. Favorable policies and data privacy trends also drive this growth, creating the need for augmented security and making two-factor authentication a global technological benchmark.
Recent stats perfectly illustrate this trend, claiming weak or stolen passwords to be blamed for 81% of data breaches, with an average cost of $4.24 million per data breach incident.
No wonder two-factor authentication is becoming a standard in all data-driven industries. Still, it can be most in demand in the fields requiring stricter security measures. Some examples include:
- Government and municipal services, where security is critical. Two-factor authentication helps to protect access to sensitive data like the location of dispatched units and staff personal information.
- Businesses using expensive equipment, like in mining and construction, benefit from two-factor authentication, as it ensures that only authorized personnel can locate the equipment and prevents tampering with control commands sent to devices.
- For data-rich industries that require compliance with stringent security standards, implementing two-factor authentication can help meet regulatory requirements and avoid potential fines and legal issues, while establishing data safety processes and protocols.
How does two-factor authentication work?
As mentioned, two-factor authentication adds an extra layer of security to user accounts. It requires two forms of identification before granting access, combining something you know (like a password) with something you have (like a phone or security token) to better protect against unauthorized access.
Two-factor authentication can be implemented in several different ways, including:
- SMS or email codes
A one-time code is sent via text or email, which the user must enter to verify their identity. - Authenticator apps
Apps like Google Authenticator or Authy generate time-sensitive codes used alongside the password. - Hardware tokens
Physical devices that generate authentication codes or connect to a device to verify the user. - Biometrics
Fingerprints, facial recognition, or voice verification to confirm identity based on unique physical traits.
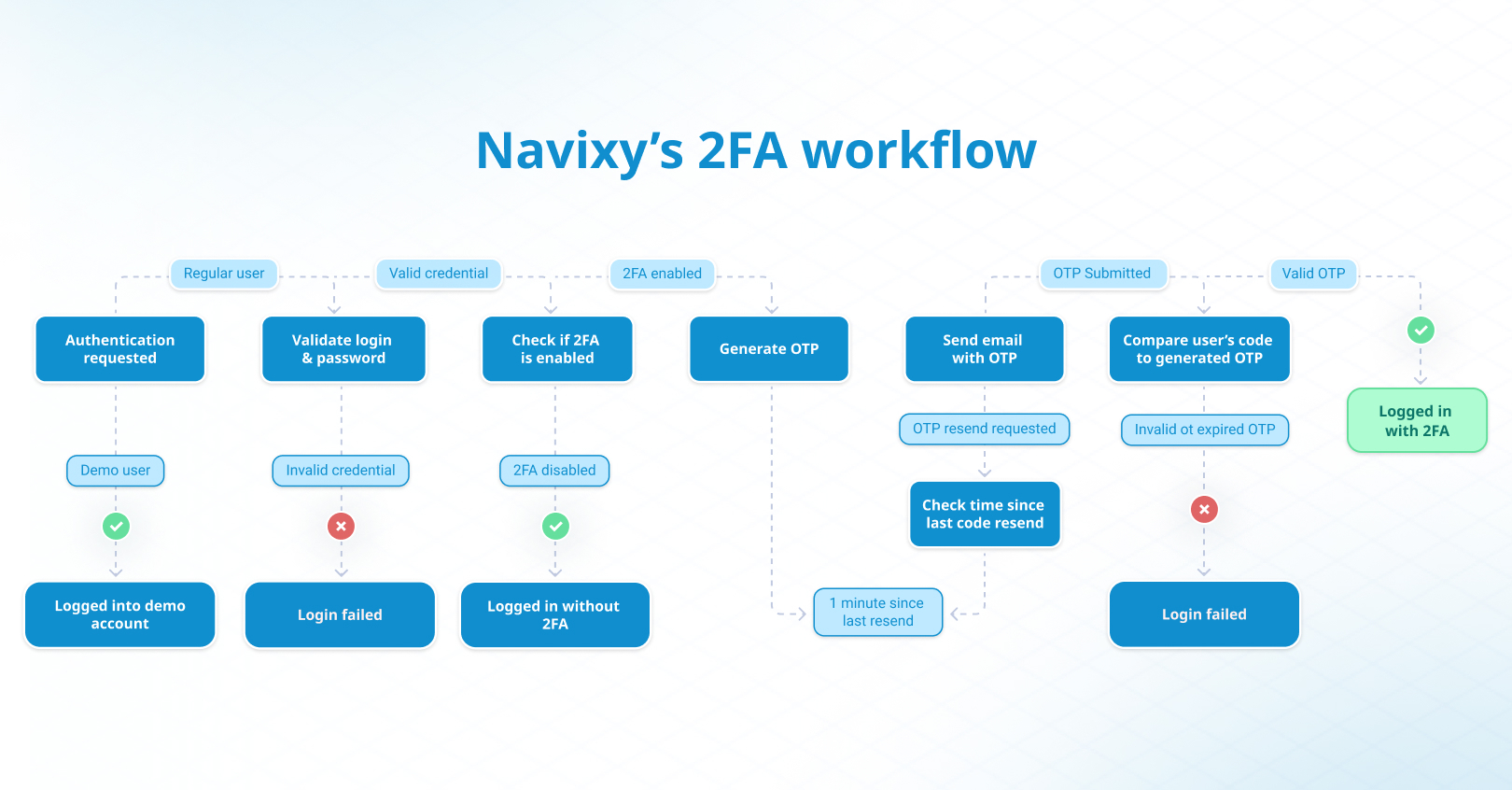
Behind the scenes, two-factor authentication takes several steps.
- The user begins by entering their username and password, as they would with a standard login.
- Once the password is verified, the system prompts for a second form of authentication, such as a code sent via SMS, an app-generated code, or a biometric scan.
- The user then provides the second factor, whether by entering the code or completing the biometric scan.
- The system checks the validity of the second factor and ensures it matches the user’s registered method.
- If both the password and second factor are correct, the user gains access to their account. If either is incorrect, access is denied, adding an extra layer of protection.
These steps ensure that even if an attacker steals the user’s password, they would still need the second authentication factor to gain access, making it significantly harder for unauthorized users to break into the account.
How is two-factor authentication realized in Navixy?
Our first stage of two-factor authentication implementation focuses on generating one-time passcodes and sending them to the email used to access the platform. Each passcode is valid for only 5 minutes, minimizing the window for potential misuse. Additional requests are limited to prevent abuse, allowing a new passcode to be requested only once every minute.
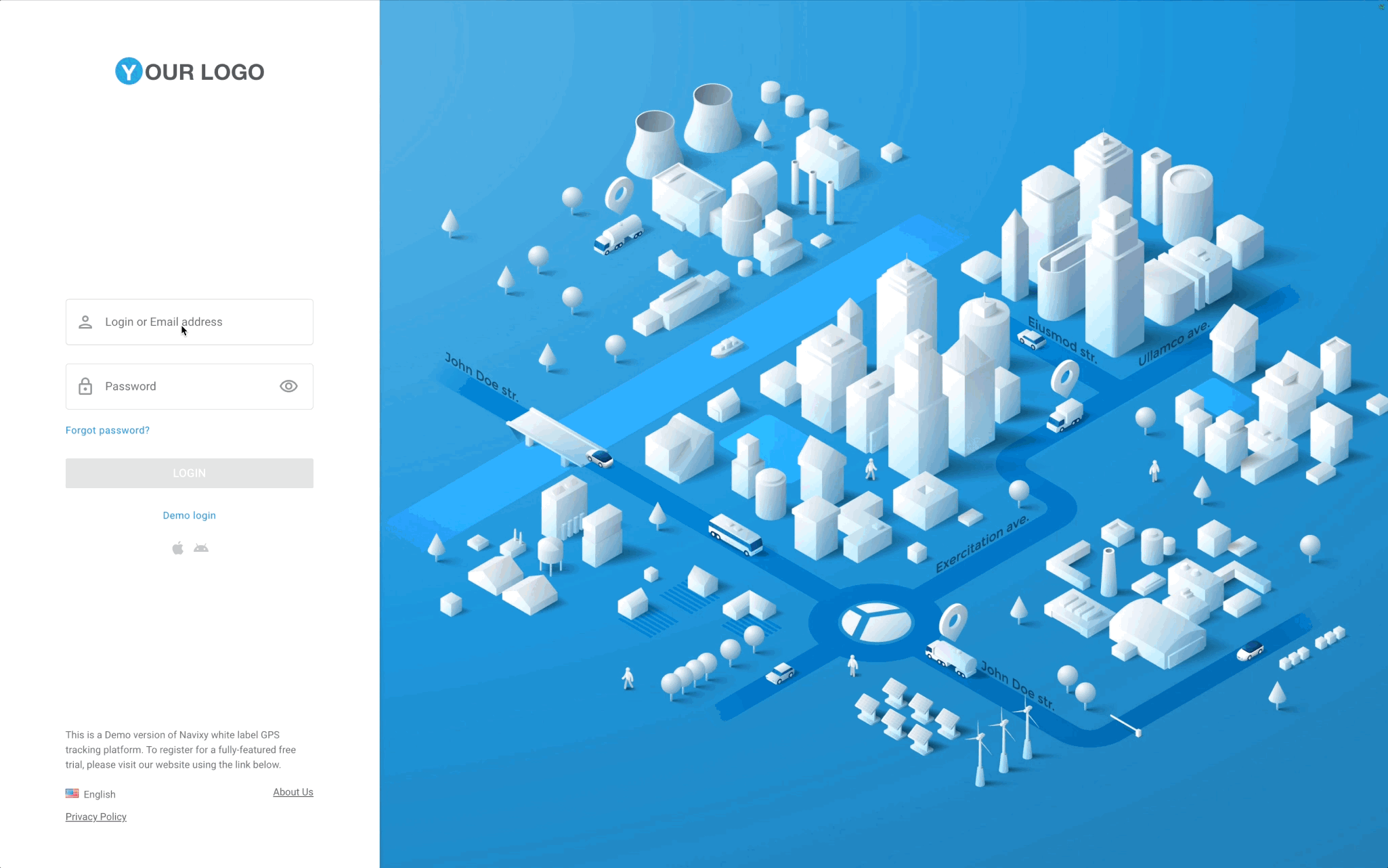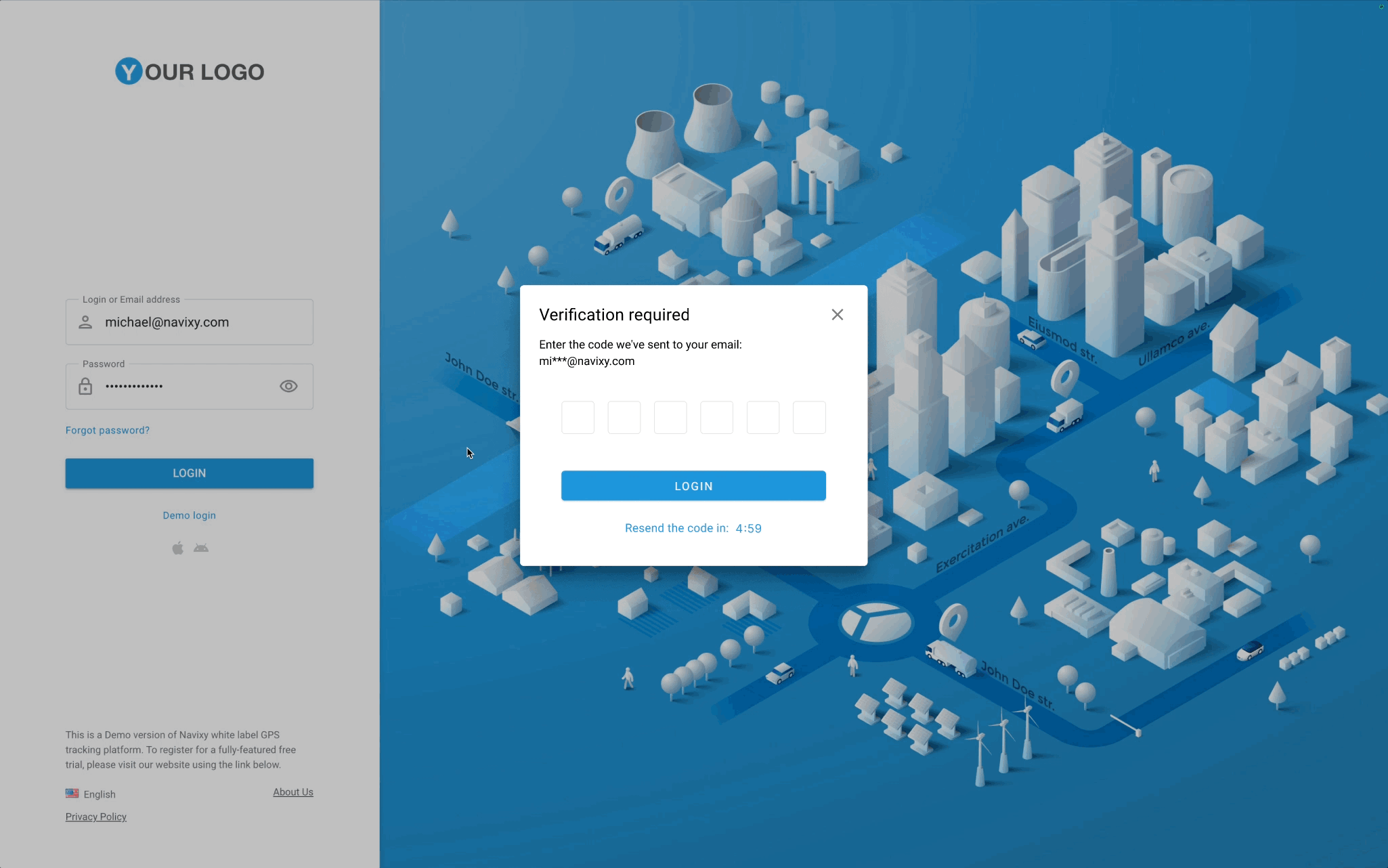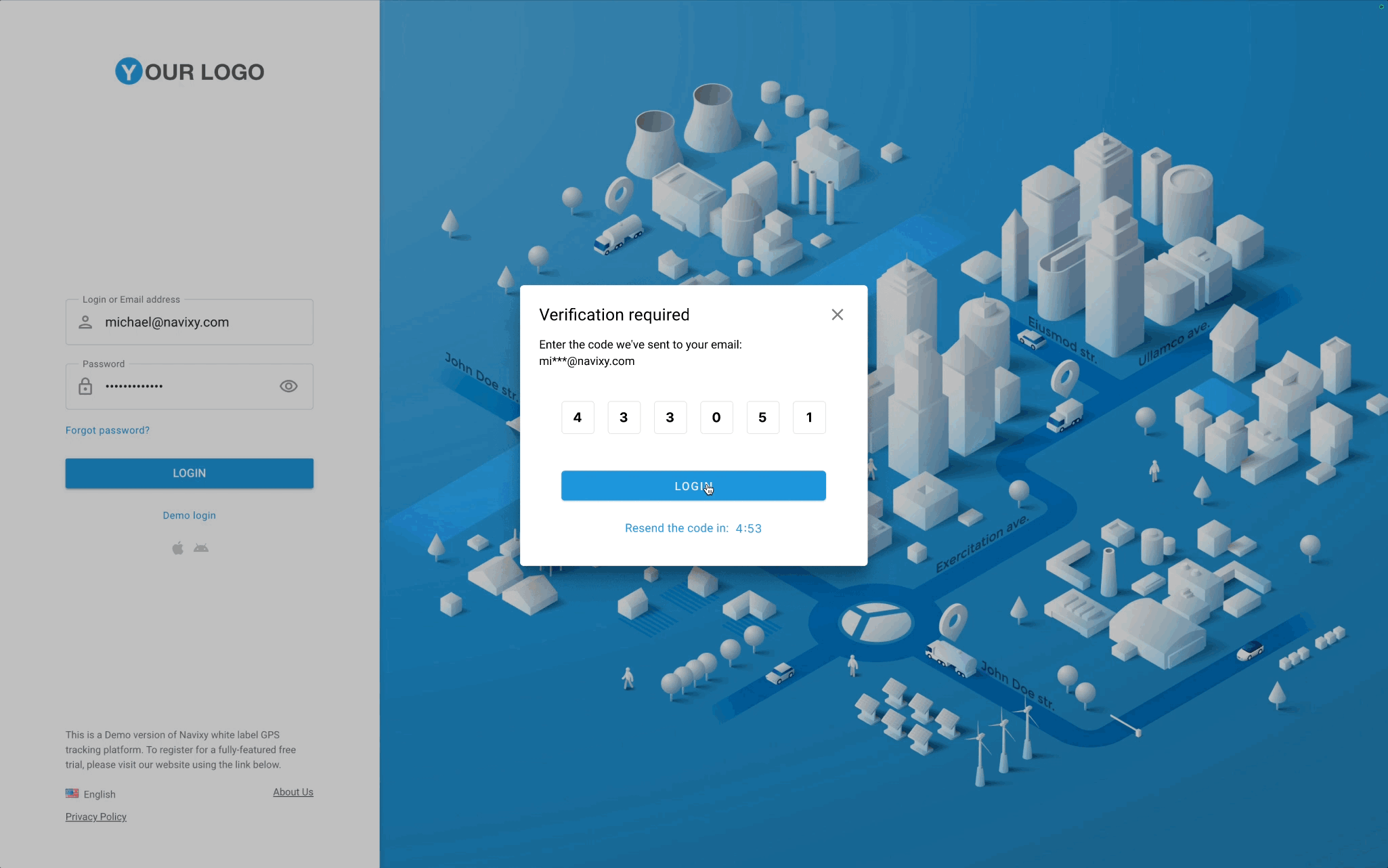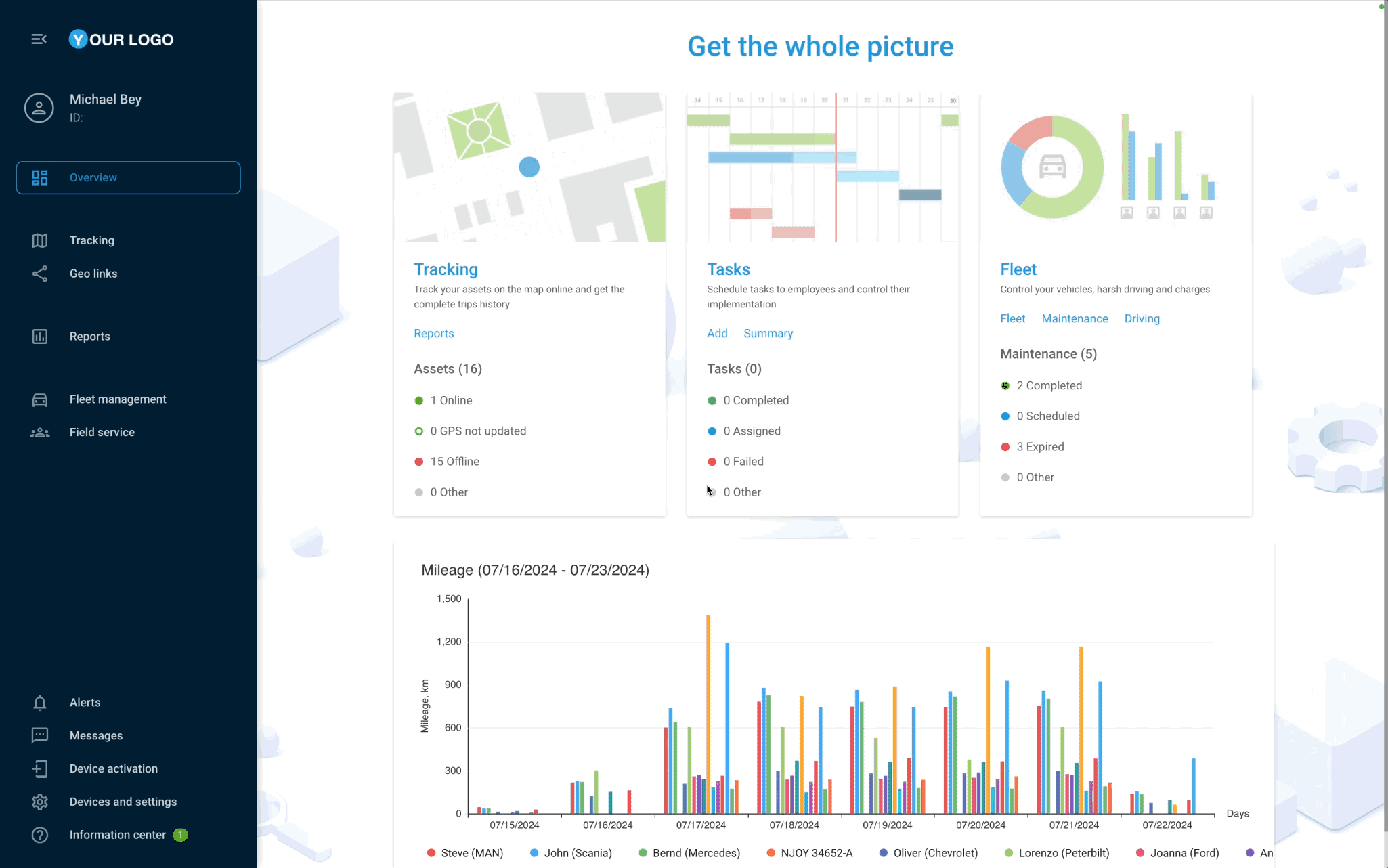
Securing the login process
Knowing that the login page is the first step in a user’s journey, we ensured minimal disruption while integrating two-factor authentication into the existing login process. The usual credential validation procedure remains the same, so the next steps are available only if the login/password combination is valid.
From the user’s perspective, there are just a couple of extra steps:
- Check the email for the one-time code. We’ll send a verification code to the email used for logging in, with an option to navigate to their account settings and reset the password if the account was compromised.
- Provide the one-time code. The passcode validation begins automatically as soon as the code is entered or pasted into the field.
For all users with two-factor authentication, a second factor validation will be performed during each log in attempt, whenever the user’s session has expired. The login process will remain exactly the same for users who have two-factor authentication turned off and for demo accounts.
Generating a one-time password
Once the user's login credentials are verified, the system generates a unique one-time password (OTP) or verification code with a limited lifetime. It is a six-digit code consisting of random digits from 0 to 9 that is valid for just 5 minutes, minimizing the risk of misuse. Only one OTP is valid during this time, ensuring all previously generated codes cannot be used for authentication.
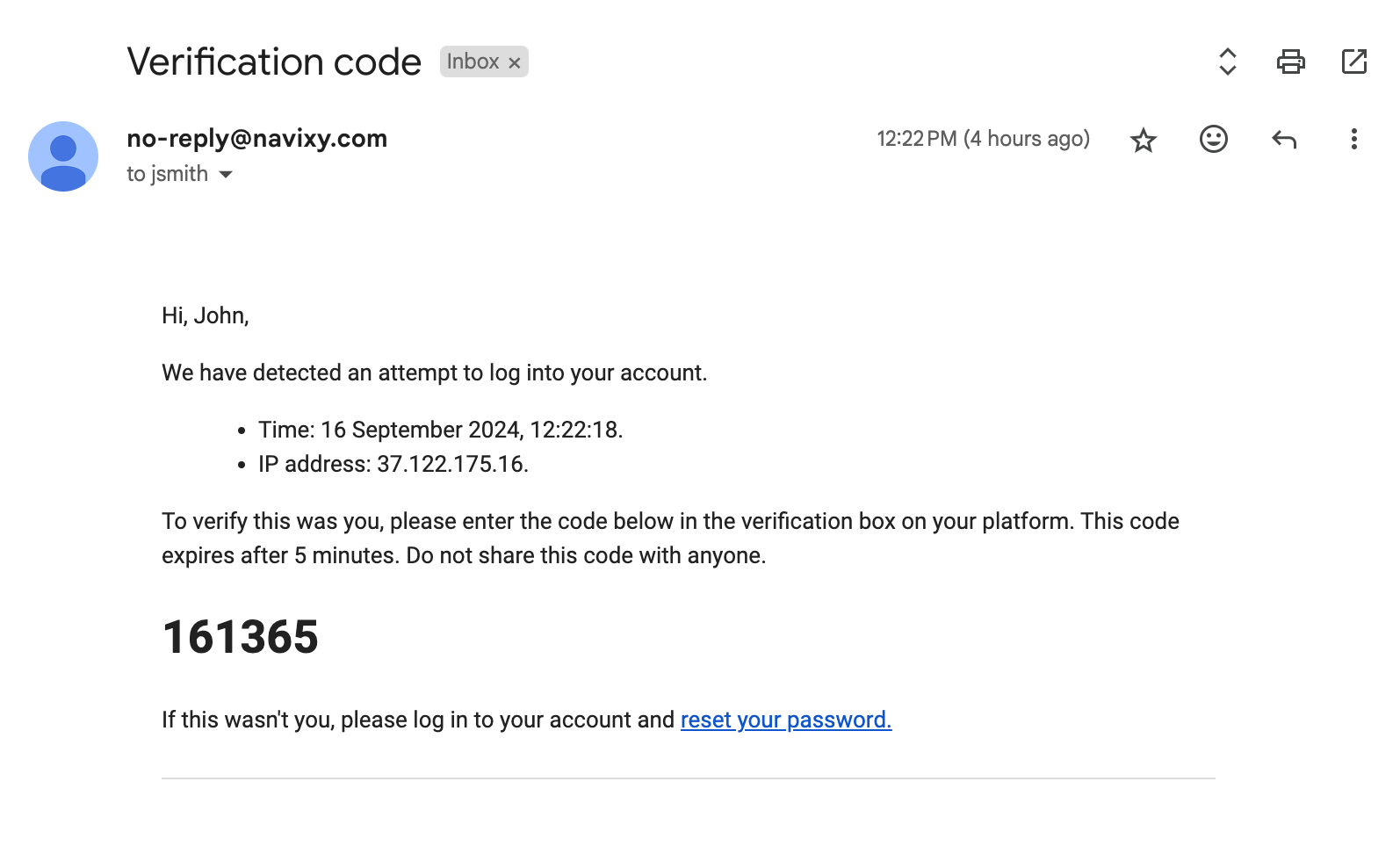
The OTP is then securely and promptly communicated to the user via the email approved during login/password validation. To prevent abuse and brute force attempts, users can request a new code once every minute. To validate the code provided by users, we check the current OTP’s lifetime. If valid, we check the actual digit sequence:
- If the user’s OTP matches the currently valid OTP, the authentication is successful. After a successful authentication, the OTP becomes invalid.
- If the user’s OTP doesn’t match our OTP or is expired, the authentication is denied, and an error message is displayed.
The number of validation attempts is limited by the authentication API call rate limit, ensuring consistent performance and security.
To further limit code guessing attempts, we’ve limited the special user session to just 5 minutes. After 5 minutes of unsuccessful code validation attempts or simply idling, the login and password are requested again, and the authentication starts from the beginning.
Two-factor authentication API enhancements
To support requesting a second factor during authentication, we’ve updated our API:
- The
/user/authmethod now returns a new special session type if a second factor is required. - Added a new
/user/auth/code/resendmethod to resend an authentication code to the specified email - To verify the code and receive the session hash, there is the
user/auth/code/verifymethod.
For a detailed review of our authentication process, refer to the Developer Documentation.
How to configure two-factor authentication
Platform administrators can adjust security settings in the Admin Panel. Currently, you can control whether to enable two-factor authentication for:
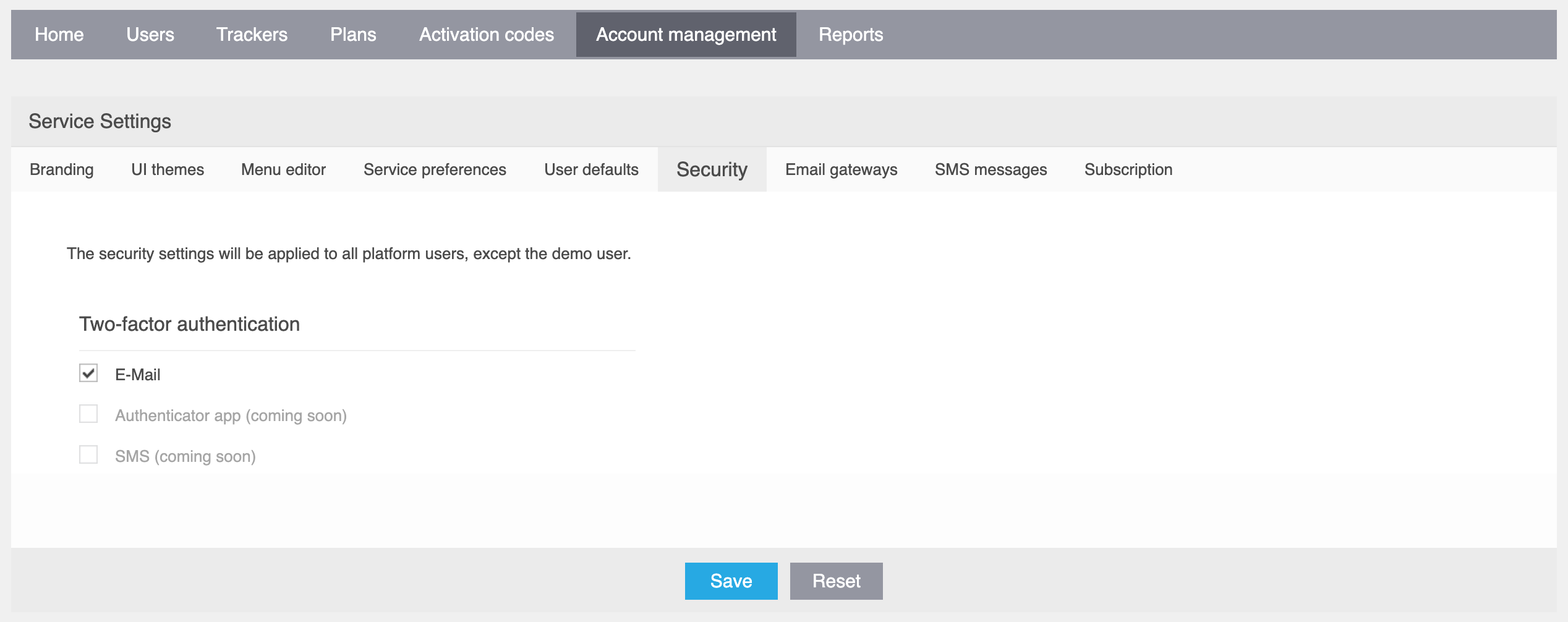
- All platform users: To make two-factor authentication mandatory for all current platform users, toggle the setting in Admin Panel → Account management → Security. This will also set the default state for all newly created users: when transferring users from another platform or importing user data in bulk, the two-factor authentication setting will be applied according to your current configuration.
- Particular users: For specific accounts requiring personalized two-factor authentication settings, go to Admin Panel → Users → Edit user → Two-factor authentication.
Note that the current implementation only allows enabling two-factor authentication for all account users, including sub-users created in the main account.
To configure 2FA settings, you can utilize our updated Panel API, using the calls to read and update 2FA settings for a list of specified users or all users of the platform, as well as set default settings for new users. Learn more about our Panel API in the Developer Hub.
Platform support
The 2FA feature is designed to work flawlessly across desktop and mobile web layouts, thanks to responsive UI practices.
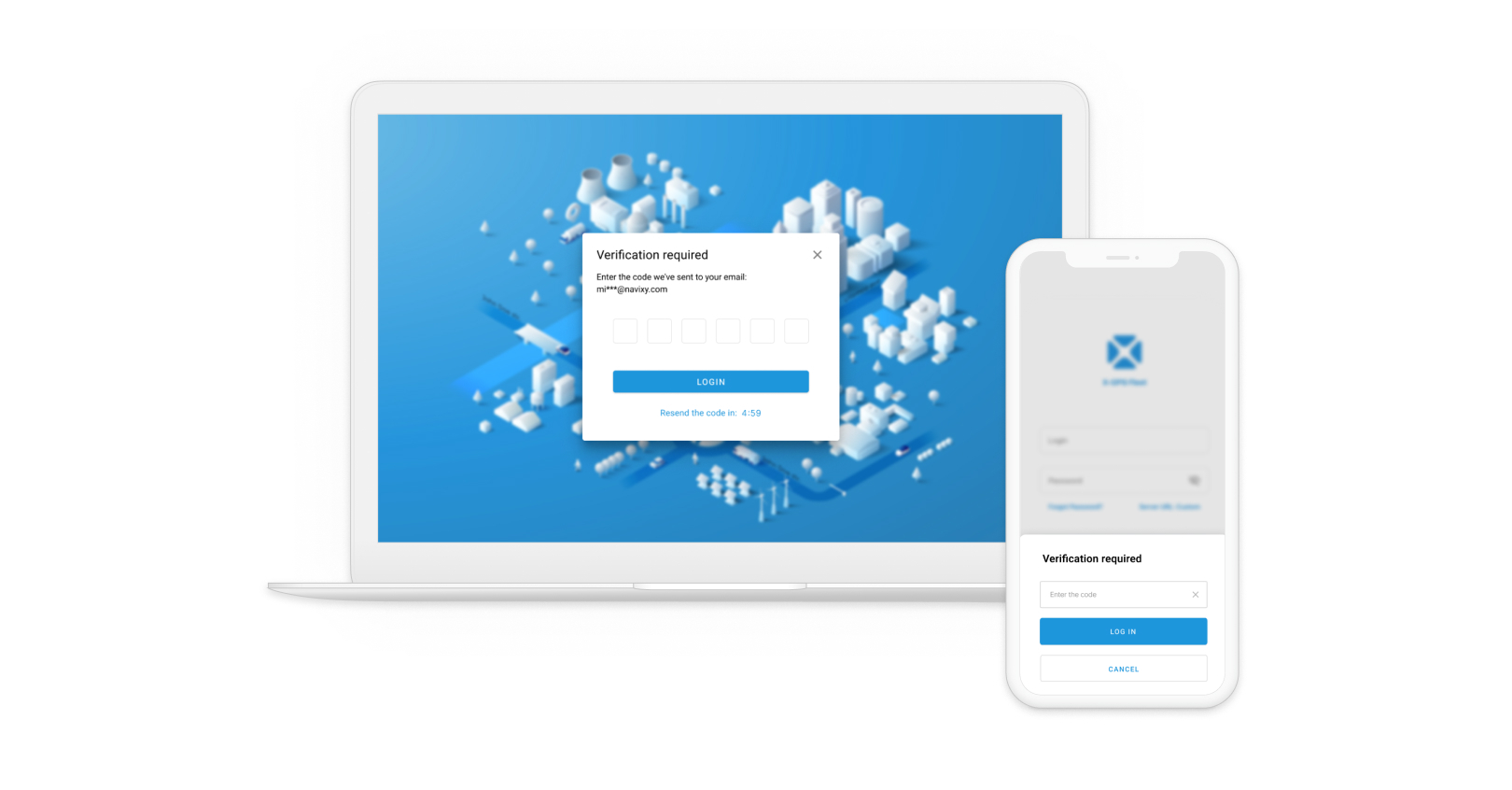
The changes will also affect the X-Monitor application for iOS and Android, and will be included in our upcoming new mobile app for fleet managers.
Conclusion: security perspectives with 2FA
The introduction of two-factor authentication marks a significant milestone in our commitment to enhancing security. Next, we envision this feature becoming more flexible and configurable:
- Allowing end-users to control security settings for their accounts and preferred 2FA methods to further mitigate threats of unauthorized access;
- Supporting more methods for receiving the second factor, such as various authenticator apps that keep the second factor secure on the user's device;
- Adding advanced configuration options for integrators and developers, such as managing passcode lifetime and resend attempt limits.
We encourage our partners to take advantage of this powerful feature and experience its benefits.